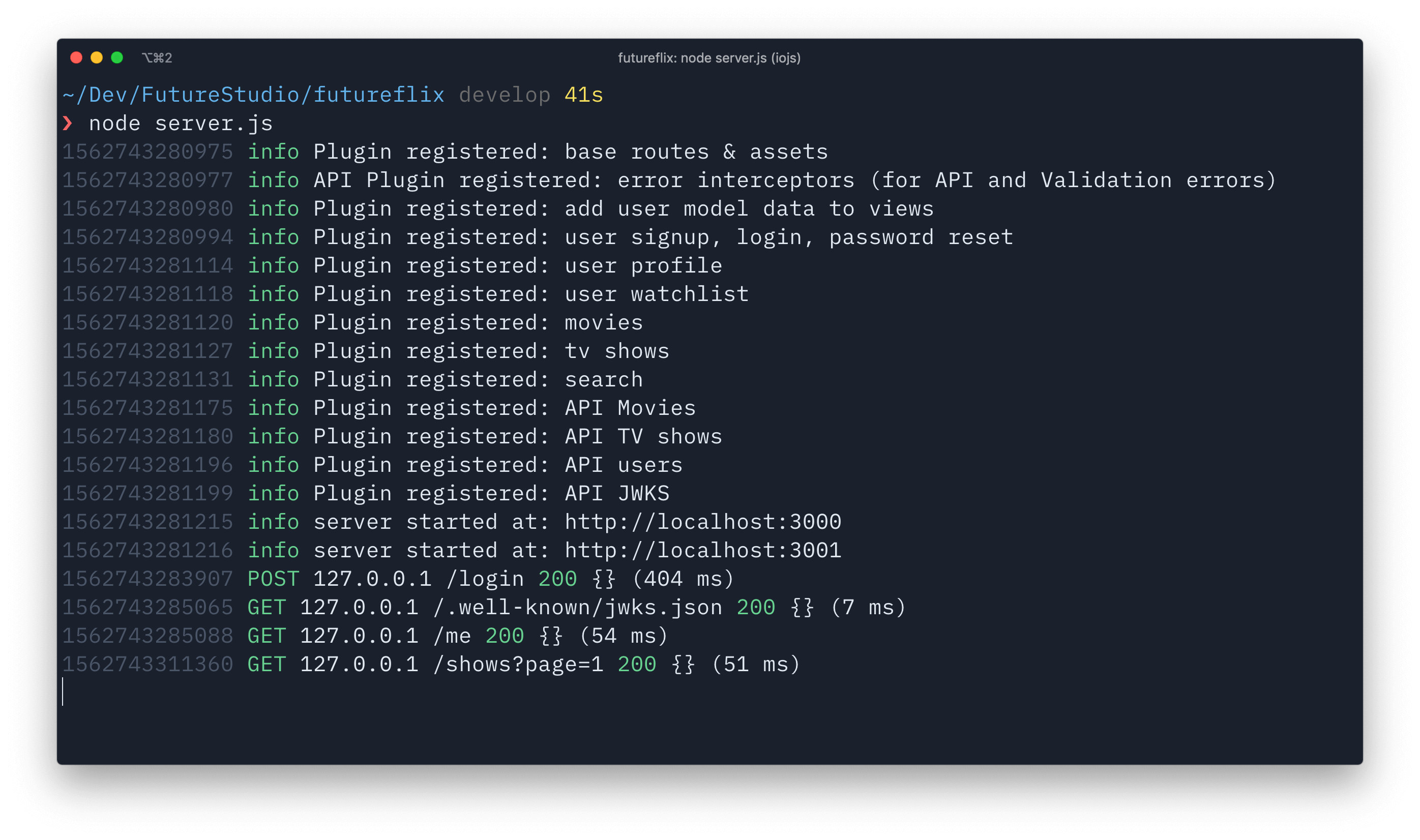
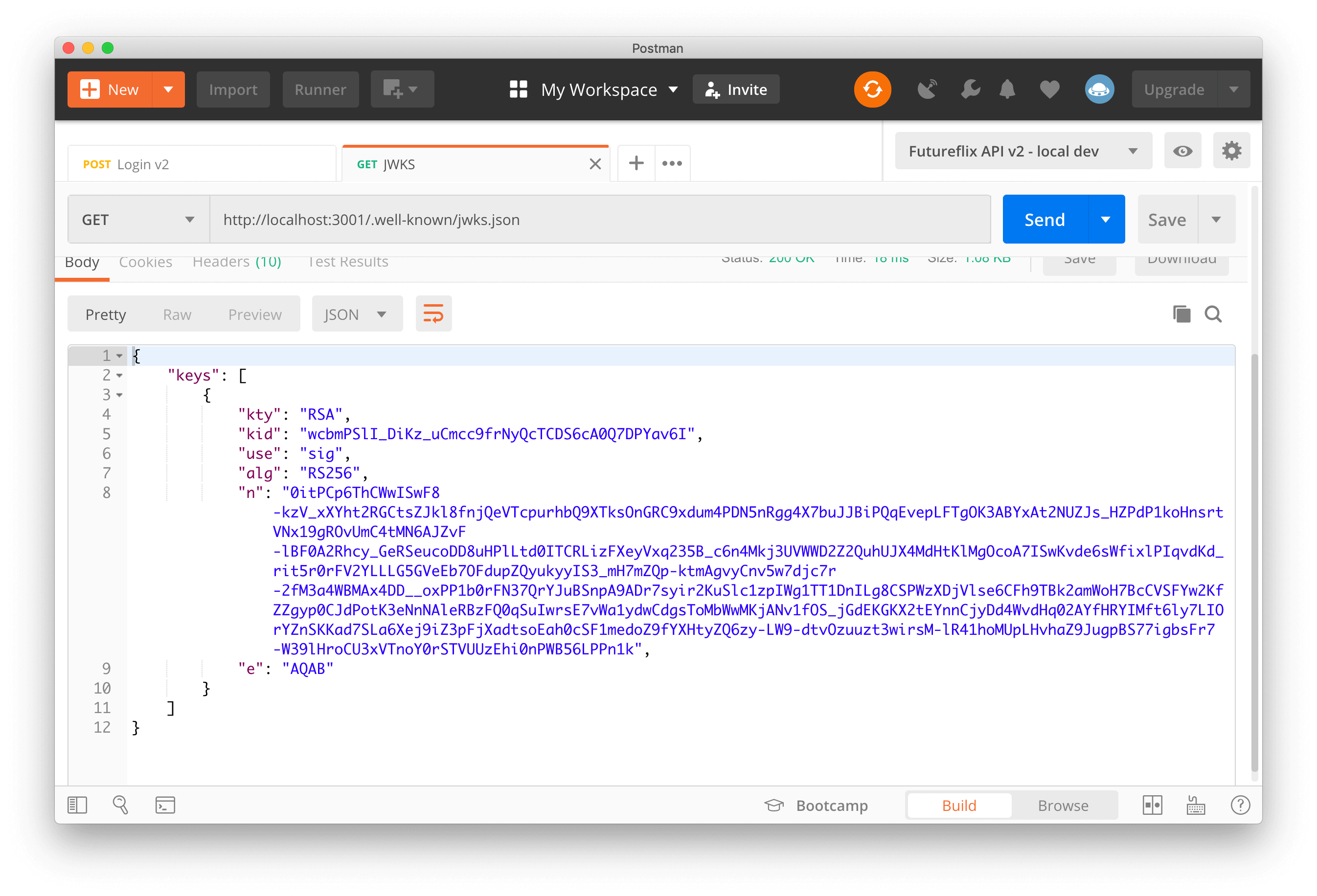
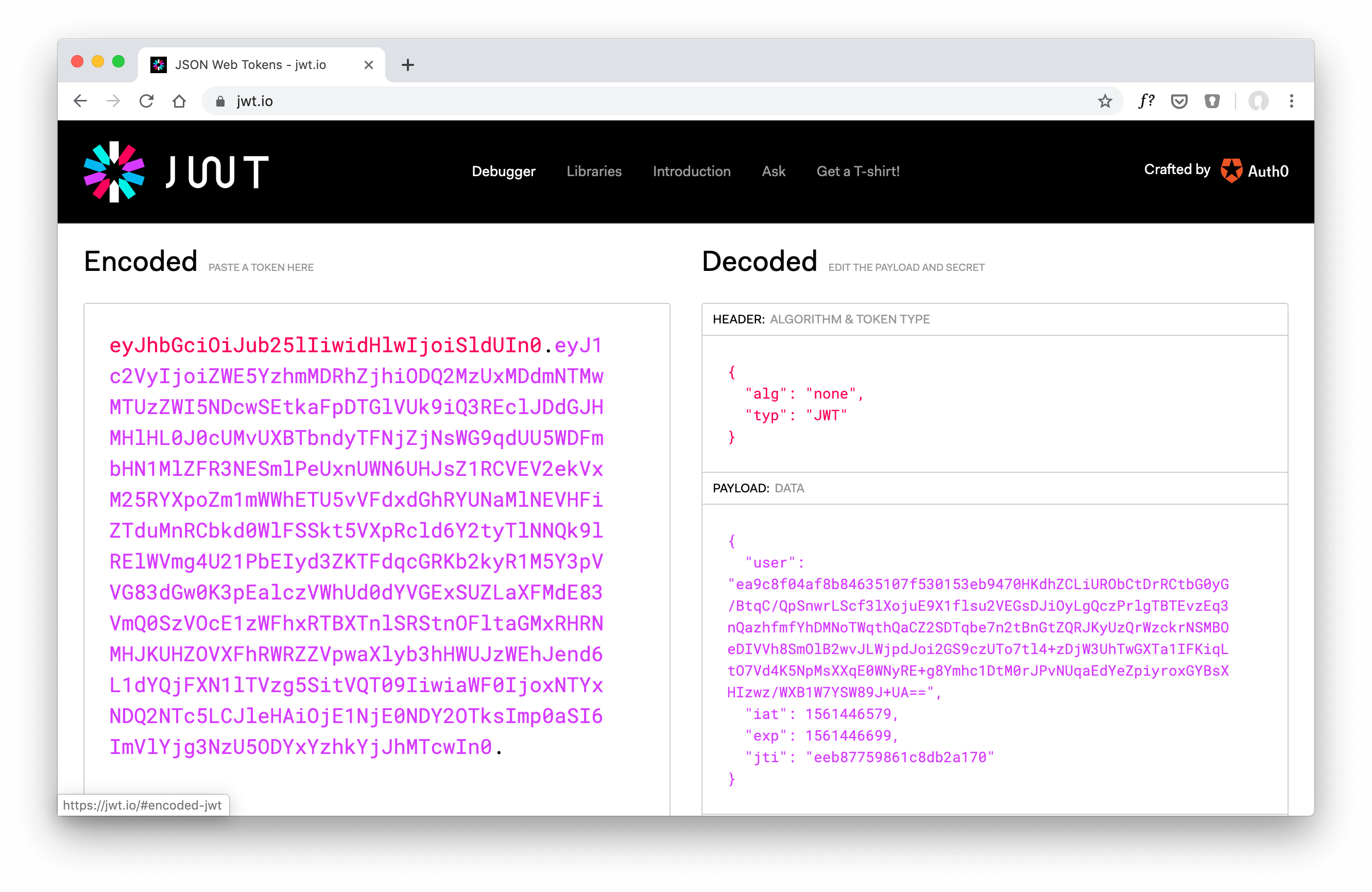
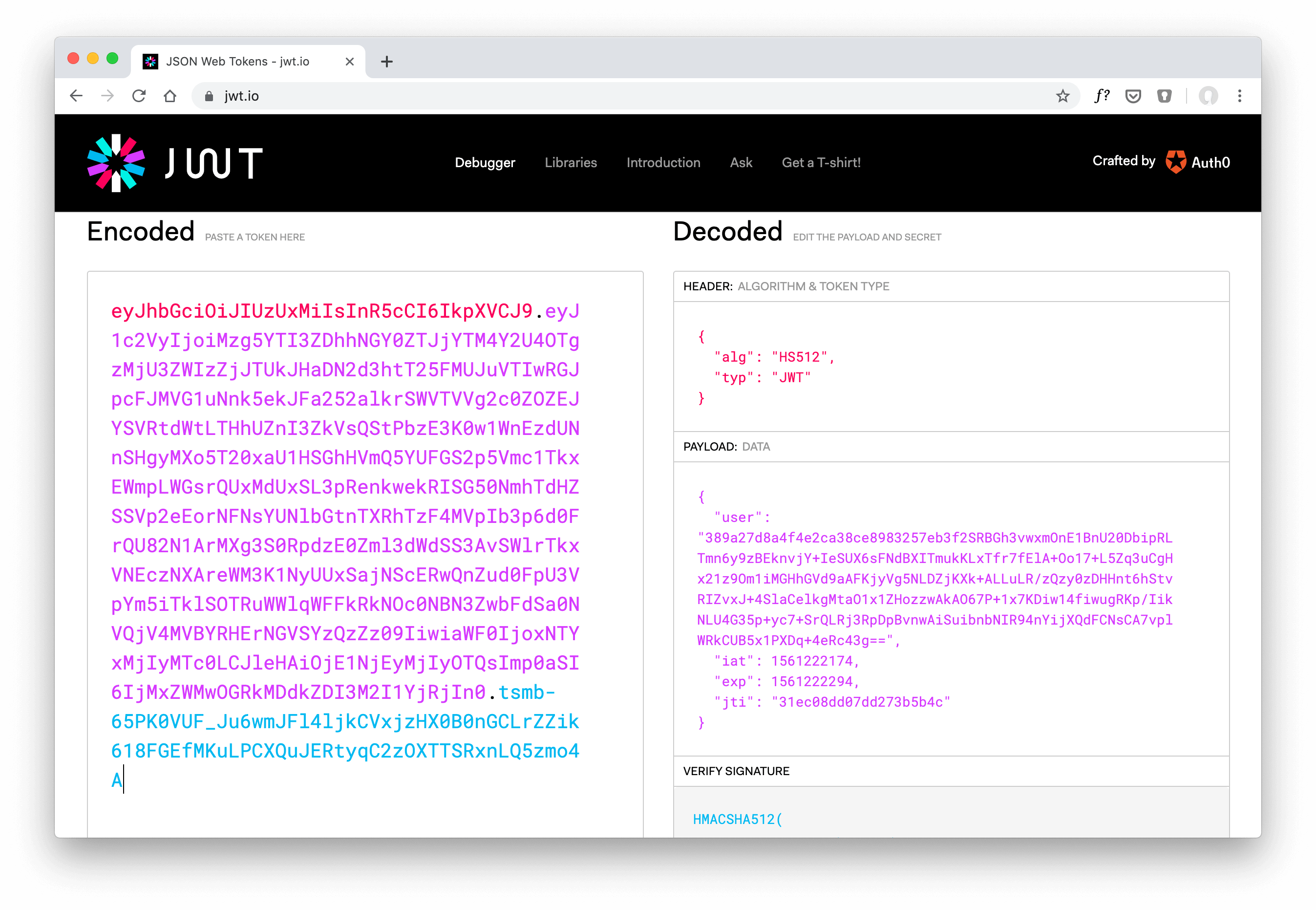
learn hapi — JWT Verification via JWKS API Endpoint
JWT authentication uses a secret to sign or encrypt the tokens. Using an asymmetric algorithm based on a public/private key pair comes with some benefits. One benefit is that you can share the public key with anyone on the Internet. Of course, you must keep your private key safe …
Continue Reading